|
RSA ClearTrust 5.0.1
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Contents
DisclosureRSA Security Inc. sponsored the testing in this report. Mindcraft, Inc. conducted the performance tests described in this report at Sun’s test lab in Menlo Park, California. AcknowledgementWe thank Sun for providing the systems used for the tests and the support staff who helped configure the servers. |
This part of the white paper analyzes the Login and Extranet Scenario performance of RSA ClearTrust Version 5.0.1. Login Results AnalysisTable 1 summarizes the Login Scenario performance as a function of the ClearTrust Authorization Server configuration and the number of entries in the directory. All of the Login Scenario tests used one Authorization Server; only the number of CPUs was varied as shown in Table 1. The RSA ClearTrust Authorization Server is the control point for all authentication and authorization. Our tests were structured to push the Authorization Server system as close as possible to 100% CPU utilization. The CPU Utilization by Server Type column in Table 1 shows that the RSA ClearTrust Authorization Server was performing at its maximum. All user credentials for the entries tested were cached in the Authorization Server, which accounts for the low directory server CPU utilization. The Web server CPUs had enough spare performance available so that they were not performance bottlenecks for the tests. The load generator (LG) systems were sufficient to create a workload on the servers that drove the Authorization Server to its peak performance. In Test #3 we did not record the load generator CPU utilization; however, the load generator systems never exceeded 75% CPU utilization for any of the Login tests. The network had enough bandwidth available to support the highest load without limiting overall performance. Table 1: RSA ClearTrust 5.0.1 Login Performance
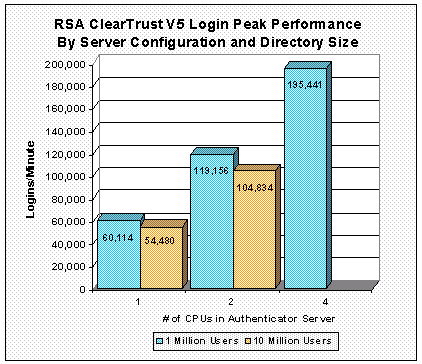
Table 1 also shows normalized metrics based on the total number of CPUs in the configurations tested and the number of CPUs in the single Authorization Server that was used for these tests. The Scaling Factor/Total CPUs in Table 1 shows how much faster on a per-CPU basis a configuration is than an Authorization Server with one CPU, the smallest Authorization Server configuration. It is computed by dividing the Logins/Minute/Total CPUs for a configuration by that for the single-CPU Authorization Server configuration. A metric close to 1.0 indicates linear scaling. A metric above 1.0 means that the configuration provides better than linear scaling while a metric significantly below 1.0 means that the configuration scales less than linearly. For the 1,000,000-user directory, the Scaling Factor/Total CPUs metric shows that performance scales linearly as the Authorization Server is expanded from one to four CPUs. Keep in mind that for the configurations tested the total number of CPUs did not double from Test #1 to #2 and from Test #2 to #3. The linear performance scaling based on the number of the Authorization Server CPUs is derived from the data in the Logins/Minute/Total CPUs column. For the 10,000,000-user directory, per-CPU Authorization Server performance also scales linearly. Figure 1 shows RSA ClearTrust's Login performance from Table 1 by Authorization Server configuration and directory size. Figure 1: RSA ClearTrust Login Performance for 1 Million and 10 Million Users Extranet Results AnalysisThe Extranet Scenario simulates customers or suppliers logging into a private Web site and obtaining information they are authorized to receive. It measures the combination of one user authentication and 10 authorizations for access to resources (these 11 Extranet operations constitute one Extranet sequence). We report the total Extranet operations per minute, which is 11 times the number of Extranet sequences. The Extranet Scenario, because it uses a more realistic mix of operations than the Login Scenario, provides a better basis for comparing access control and identity management solutions. You can find a more complete description of the Extranet Scenario below. The Extranet test was done with RSA ClearTrust configured to cache user credentials, as one would do if the servers were on the inside of a private network with firewalls to protect access to systems that store passwords and other sensitive information. We call this a full-cache configuration. Table 2 shows the Extranet Scenario performance of RSA ClearTrust with 1,000,000 users in the directory. As with the Login Scenario, the Extranet Scenario simulates the activities of 10% of the number of users in the directory, which in this case is 100,000 users. The Extranet Scenario tests were structured to push the Authorization Server system as close as possible to 100% CPU utilization. The CPU Utilization by Server Type column in Table 2 shows that the Web servers' CPUs had enough spare performance available so that they were not performance bottlenecks for the tests. At 10% CPU utilization, the directory servers were lightly loaded and did not limit overall performance. Similarly, the network had enough available bandwidth that it did not limit SUT performance. Table 2 shows that the RSA ClearTrust Authorization Server was performing at its maximum for Test #6 but still had available CPU time for authentications and authorizations in Test #7. We were not able to push Test #7 to fully utilize the Authorization Server's two CPUs because we did not have enough load generating systems available, which can be seen in their high 83% CPU utilization. Having insufficient computing resources is not uncommon given the exigencies of performance testing. If there had been enough load generating capability, the same SUT would have achieved higher performance. Table 2: RSA ClearTrust Extranet Performance - 1 Million Users in the Directory
The Scaling Factor/Total CPUs in Table 2 shows how much faster on a per-CPU basis the two-CPU Authorization Server configuration is than the one-CPU configuration. It is computed by dividing the Extranet Operations/Minute/Total CPUs for the two-CPU configuration by that for the one-CPU configuration. This metric clearly shows that performance scales better than linearly as the Authorization Server is expanded from one to two CPUs. This more-than-linear scaling occurred in part because we were able to saturate the Authorization Server in the one-CPU configuration while having excess Web server CPU capacity. In other words, we could have used fewer Web server CPUs and achieved the same level of performance for the one-CPU Authorization Server configuration. ConclusionsThese AuthMark Benchmark results lead us to conclude that:
Test MethodologyMindcraft® tested the performance of RSA ClearTrust using our iLOAD MVP™ tool to run the AuthMark ™ Benchmark Login and Extranet Scenarios. We describe these tests below to further your understanding of the performance results discussed above. iLOAD MVP OverviewiLOAD MVP is a general-purpose, script-driven capacity planning, benchmarking, and regression testing tool. The major components of iLOAD MVP are:
iLOAD MVP provides the capabilities needed to test high-performance servers with a small number of client systems. Its capabilities include:
The AuthMark BenchmarkThe AuthMark Benchmark is designed to test the performance of products that provide authentication and authorization services in support of Web servers. Authentication is the process of verifying who a user is; it typically occurs when a user logs in. Authorization is the process of verifying that an authenticated user is allowed to see or to use a particular resource. In the case of a Web server such resources include HTML files, graphic files, and programs that generate Web pages dynamically. AuthMark simulates a large number of users accessing Web servers via their browsers. This approach permits AuthMark to test authentication and authorization performance independent of the technology used to provide those services. AuthMark consists of several test scenarios to determine various aspects of performance for authentication and authorization systems under different circumstances. AuthMark Login ScenarioThe AuthMark Login Scenario focuses on testing authentication. We call it the Login Scenario because authentication is done the first time a user accesses a protected part of a Web site, just like a login. The HTTP 1.0 and 1.1 protocols define the steps a browser follows for authentication. Some of the steps are visible to you and others are not. It is important to understand what happens during a login in order to understand what the Login Scenario measurements mean. Login ProcessThe following simplified sequence will walk you through the login process to show how it works using the HTTP 1.0 and 1.1 protocols:
Notice that the URL you clicked on or entered is actually sent twice (in steps 1 and 6). This means that the authentication system is used twice—first, it finds out that the requested URL requires the user be authenticated, then it processes the authorization header when the request is resent. Once a user has been authenticated, a Web browser automatically sends the authorization header whenever the user requests a URL in the same realm requiring authentication. Login Scenario ConfigurationTable 3 shows the AuthMark Login Scenario configuration parameters we used. Table
3: AuthMark Login Scenario Configuration Parameters
The number of user sessions active during a given test run is determined by the length of the test and the number of logins. Sessions are not logged out once created. Instead, each session remains quiescent after login. Running the Login ScenarioThe basic steps for running the Login Scenario are:
The Login Scenario test script selects users randomly from those in the directory (see Table 3 for the numbers we used for this test). The tester is free to select the number of load generator systems and the number of iLOAD MVP client threads to use. These are called the load generators. The tester selects the number of load generators to get the highest performance possible from the authentication/authorization system being tested. In order to obtain peak performance, the tester may need to use multiple Web servers and directory servers. The tester is permitted, but not required, to do a warm-up run of the test scenario in order to get the servers to a state that would more likely represent the state they would be in during normal operation. For this benchmark, we warmed-up the servers by running each test script in its entirety. Extranet ScenarioThe Extranet Scenario simulates an environment where users must login to a Web site and where all access requests require authorization. This scenario depicts a more realistic usage pattern than the Login Scenario. The Extranet Scenario test execution starts with the same operation sequence as the Login Scenario (steps 1 - 8 above) and continues with the following operations:
The Extranet Scenario sequence consists of a total of 11 client operations per user session:
RDA ClearTrus tchecks the continuing validity of an authenticated user each time a resource access request is made to ensure that the user session has not been revoked. However, the user is not re-authenticated. As a result, the user does not see a new login request as long as the resources being accessed are in the Internet domain in which the user has been authenticated. For the Extranet Scenario, we warmed-up the servers by running the test script in its entirety. Extranet Scenario ConfigurationTable 4 shows the AuthMark Extranet Scenario configuration parameters we used.
Sessions are not logged out once created. Instead, each session remains quiescent after all of its requests have been satisfied. Running the Extranet ScenarioThe basic steps for running the Extranet Scenario are:
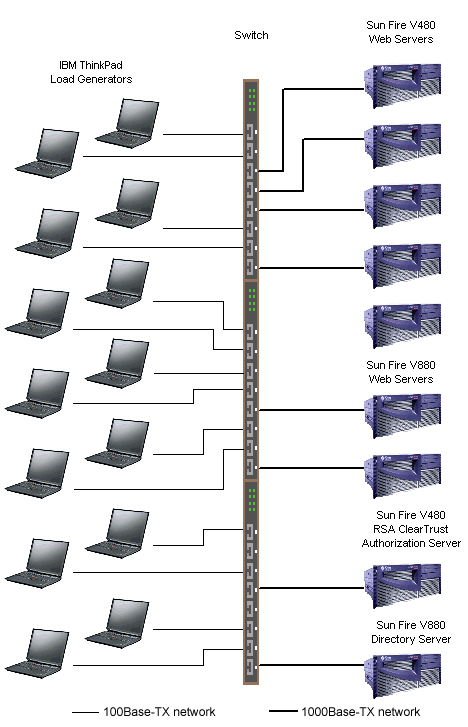
The Extranet Scenario test scripts select users randomly from users in the directory (see Table 4 for the numbers we used for these tests). The tester is free to use any number of load generator systems each running any number of iLOAD MVP client threads (called load generators). The tester selects the number of load generators to get the highest performance possible from the authentication/authorization system being tested. In order to obtain the peak performance, the tester may need to use multiple Web servers and directory servers. The tester is permitted, but not required, to do a warm-up run of the test scenario in order to get the servers in the state they would be in during normal operation. For this benchmark, we warmed-up the servers by running the test scripts in their entirety. Server Hardware and Software Set UpMindcraft used three types of servers for these tests: Web, Authorization, and directory servers. Table 5 shows the summary of the server configurations and the number of load generators we used for each test. The detailed configurations of the RSA ClearTrust Authorization Server and the directory server are shown in Table 6 and Table 7, respectively. Tables 8 and 9 show the Web server configurations. Figure 2 shows how the various servers were connected for the tests; however, you will need to refer to Table 5 to see which systems were used for each test. Table 5: Servers and Load Generators
Table 6: RSA ClearTrust Authorization Server Configuration - Sun Fire V480
Table 7: Directory Server Configuration - Sun Fire V880
Table 8: Web Server A Configuration - Sun Fire V480
Table 9: Web Server B Configuration -Sun Fire V880
Figure
2: Test Lab Configuration Load Generator SystemsWe used up to 14 IBM ThinkPad laptop computers as load generator systems for these tests. Table 10 details the configuration of the load generator systems. Table 10: IBM ThinkPad Configuration
NOTICE: The information in this publication is subject to change without notice. MINDCRAFT, INC. SHALL NOT BE LIABLE FOR ERRORS OR OMISSIONS CONTAINED HEREIN, NOR FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES RESULTING FROM THE FURNISHING, PERFORMANCE, OR USE OF THIS MATERIAL. This publication does not constitute an endorsement of the product or products that were tested. This test is not a determination of product quality or correctness, nor does it ensure compliance with any federal, state or local requirements. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||

Mindcraft is a registered trademark of Mindcraft, Inc.
Product and corporate names mentioned herein are trademarks and/or registered trademarks of their respective owners.
For more information, contact us at: info@mindcraft.com
Phone: +1 (408) 395-2404
Fax: +1 (408) 395-6324